Read closely because you if haven’t experienced these, you will!
We are lucky to live in a time of amazing technical innovation because every day there is a new, more convenient way of accessing, sharing, and consuming information. The speed at which we work, communicate, and complete tasks has accelerated immensely from 30 years ago. However, with all great innovation come those who want to use it for criminal purposes.
One of the biggest technical innovations to affect our business and personal lives in the last 30 years is email. We rely on it daily and demand constant availability. This dependency makes it an appetizing vehicle for cybercriminals to use for attacks. As a result, they developed and continue to develop multiple methods to attack, posing a severe threat to organizations everywhere. What can you do?
Let’s explore 6 of the top ways cybercriminals are trying to trip you up!
Attachments: 48% of malicious email attachments are constituted of Office files. Fake invoices are the #1 disguise… according to Symantec’s ISTR 2019 report.

Email attachments are are common and simple method cybercriminals use because it only requires an email address and a viral attachment to execute the attack. They rely on the fast-paced nature of business and the natural curiosity of people to open the attachment without considering the risk . For improved success rates, attackers use some logic when picking content and targets. Examples of this logic are sending resumes to HR, invoices to accounts payable, and memos to admins that appear to be from their boss (Impersonation is discussed a bit later) because of their familiarity and relevance to their role.
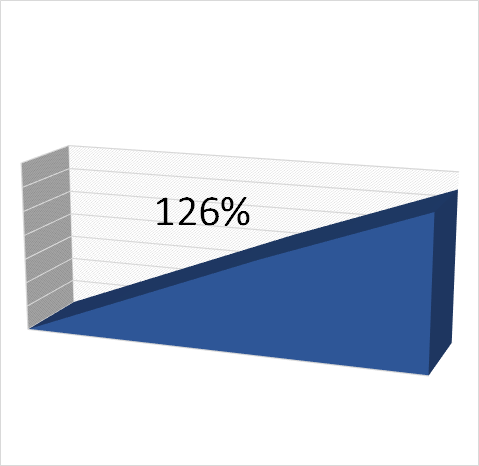
Links: One in 61 emails in corporate inboxes contains a malicious link, a 126% increase from Fall 2018 to Winter 2019…according to Mimecast’s findings
Curiosity is a fantastic human characteristic that leads to intrigue, discovery, and innovation. Curiosity is also the characteristic that compels us to click on a link in an email, contradicting what we know to be right. That is what cybercriminals are banking on. To improve the chances of a click, the attacker often “spoofs” a Web address so it appears familiar to the eye, but in reality the destination does not match. The actual Web destination sends you down a dark path to infection, credential theft, and/or data loss.
Impersonation: 67% of corporate inboxes received an Impersonation Attack in 2018. Nearly three-quarters hit with impersonation attacks reported loss of money, customers, and data, according to Dark Reading.
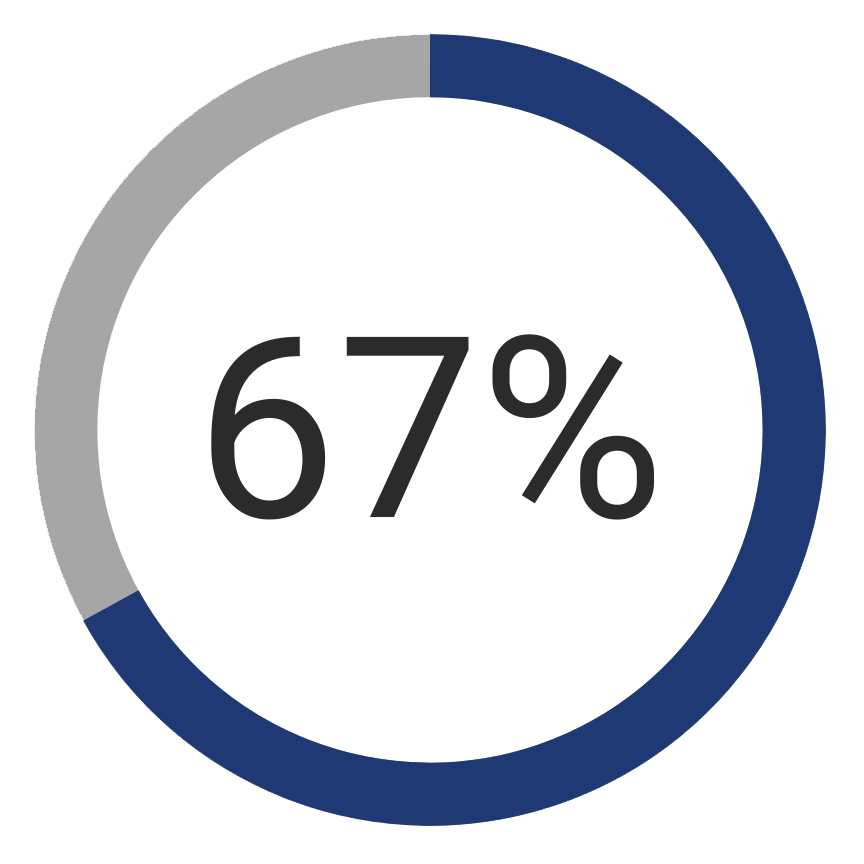
Impersonation…sounds straightforward, right? It is, and people are easily deceived by it! Email addresses are simple to create and you can essentially create one for any name in the world. You can even configure the From: field to appear as any person’s name. Since it is that easy, cybercriminals will do just that and attempt to get an email recipient to perform some action because of their trust in the sender.
Ever get an email from Aunt Emily asking you to send money to the UK because she is in a bind? It looks like her name in the header of the email but the request seemed odd. You probably thought her email was hacked, but in reality the email address is not hers at all. Inspect the From: field or email header details and you will realize it was sent from a completely different email address than the one Aunt Emily has had for 20 years. Thus, her actual email was not affected or infiltrated in any way. It is just a criminal using impersonation tactics to look familiar to the target of the email. Once again, it’s about improving the likelihood of the email being opened and the the target performing the intended action of the attacker (click, call, provide credentials, etc.).
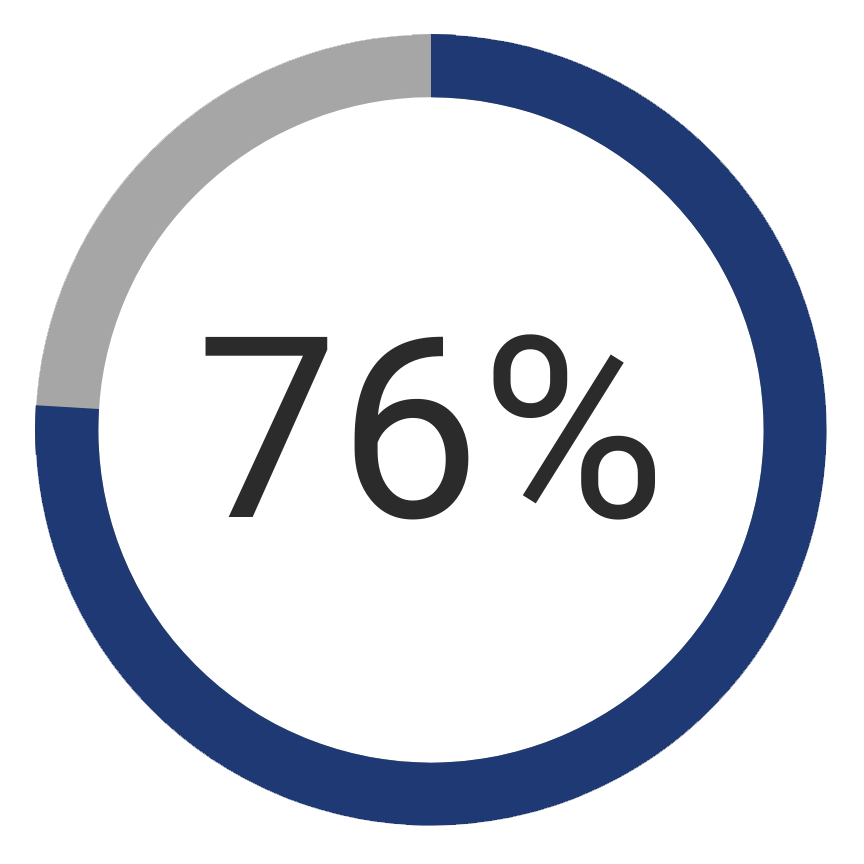
Phishing: 76% of organizations and businesses were phishing targets, according to Wombat Security’s State of the Phish 2018 report.
Duped! We have all been duped in one way or another over the course of our lives. Phishing is an attempt by a cybercriminal to deceive their target into clicking a link, performing an action, or handing over credentials. The objectives for a phishing attempt can vary, but the story below is a common example.
You receive an email you believe is from your bank (impersonation at play here) requesting you immediately log in and change your password due to a security policy change. The logo in the email seems correct, the link to connect and fix the issues is right there, and the web address seems familiar so you click away. Off you go to a website to enter your username, old password, and a new password. Problem solved! Or is it just beginning?
The issue is that the Web address on the screen was not the actual destination. You were redirected to a “spoofed” copy of the bank’s password reset page, hosted on the criminals’ servers somewhere on the globe. By entering the credentials into the seemingly safe and familiar bank login page , you just provided your active username, active password, and potential future password. Your bank account has been breached, you helped, and you didn’t even know it.
Whaling (AKA Business Email Compromise): 30% of whaling emails are opened by the targeted user with 12% taking action. This has resulted in the $12 Billion dollars in losses from 2013 to 2018 according to the FBI

Hey, if I can catch a Phish, why not go big and catch a Whale! Whaling is a lot like Phishing and Impersonation combined, but the thieves are more targeted and have much larger goals. In most cases, the target is a subordinate of a powerful C-Level individual with authority to make financial decisions. The cyber thief prepares an impersonated email and sends to the subordinate that commonly transacts the requests of a C-Level individual (think executive assistant, accounts payable, finance, etc.). If the subordinate is tricked (transfers money, buys large ticket items, provides banking credentials, etc.), it can and has resulted in millions of lost dollars.
Email Credential Theft: 40% of enterprises interviewed by Cyren and Osterman research stated they had Office 365 login credentials compromised
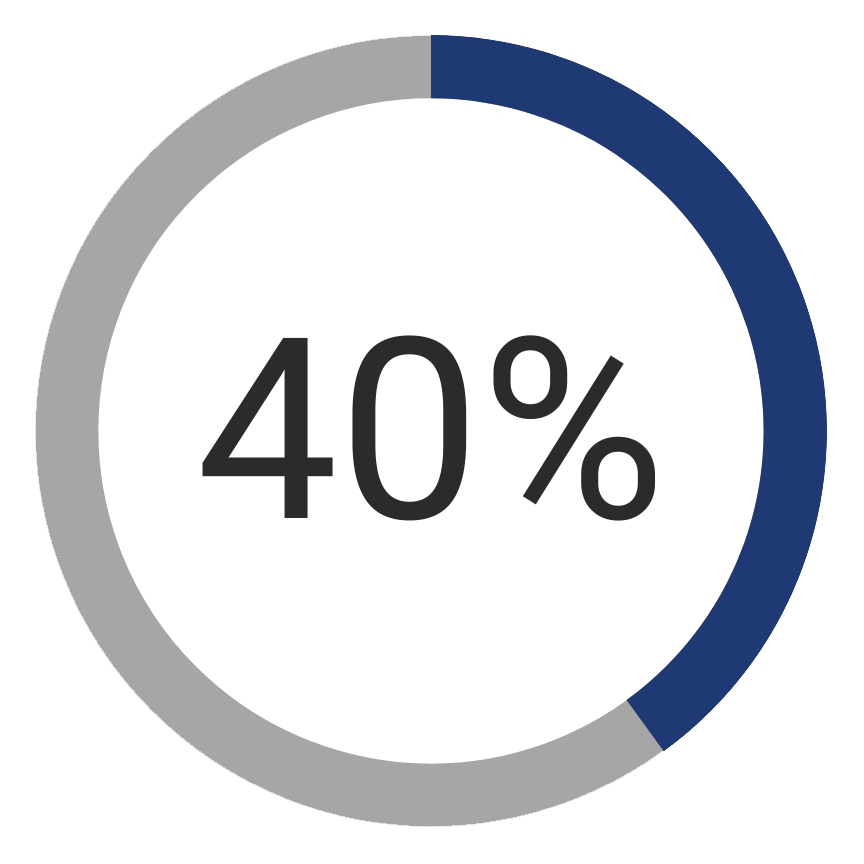
Wait, I thought that was Phishing? Yes, Phishing can have the objective of stealing credentials, but not necessarily email credentials. As an alternative to phishing, some cybercriminals us brute force hacking techniques to uncover email credentials. Others search the Dark Web for credentials stolen in breaches of 3rd parties or use. However achieved, gaining access to email credentials is a bit more broad and potentially more powerful than gaining credentials to one specific site.
Consider what someone can do if they have access to your email account.
- Access password reset emails for any site you have your email address listed
- Create new website registrations in your name
- If Microsoft Exchange is used for email, they could use those same credentials to access data in other parts of the network.
- Send threat laden email internally and externally from your trusted & recognized email address
- Turn your email into a SPAM BOT.
As more companies move to the cloud for email, credential theft rises right alongside. Many organizations fail to realize their responsibility in protecting their cloud email as they would have protected onsite email. This too has become a great opportunity for cybercriminals.
Summary: Email is the #1 Vector for delivering malware, ransomware, and initiating data theft. Criminals use email to engage end users using various different methods. Fortunately, the combination of the latest preventative protections, active system monitoring, and recurring user training has proven to be effective at stopping email borne threats. What actions are you taking?
Contact Runwell Solutions today to discuss how layers of Email security can help you develop an email security plan.

