cyber criminals new TACTICS INCLUDE EMAIL FILTERING EVASION AND EXPLOITING THE CORONAVIRUS HYPE
THE email LOOKs LEGIT, AND PRotection TOOLS THINK SO TOO
The recent wave of well-crafted phishing emails are coming from businesses you know and trust. Law Firms are commonly the sender. The emails include legitimate sender information and are sent from official company email addresses. The web links are legitimate and void of malicious content. These emails are sent from companies’ compromised email servers, and thus are delivered uninhibited by email protection solutions.
Here is how the attack works:
- You receive an email from a legitimate email address with a company name in the subject and a brief message about sharing a document or a secure message.
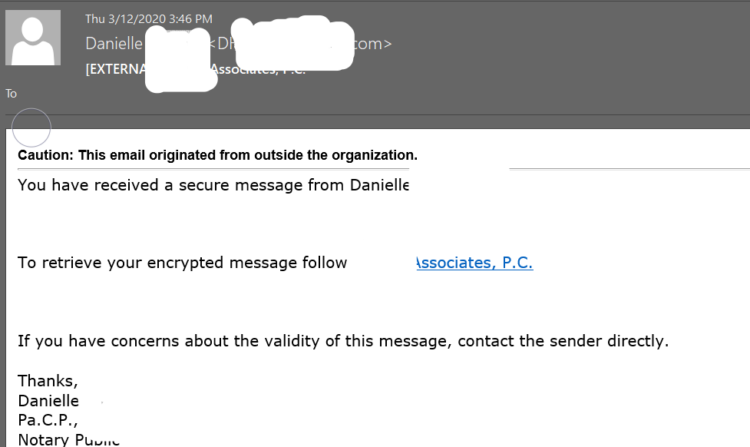
- The first link in the email shows a safe-looking link including the company name, but points to a site hosted somewhere else (e.g.: the hyperlink may read “Lawfirm & Associates P.C.”, but the underlying link does not take you to www.lawfirmassociates.com).
- Clicking the link take you to a simple site with the sender company’s logo and contact information. It looks convincing and all the information appears valid.
- HOWEVER, the webpage link on this site is where the malicious activity begins.

- The link on the landing page (in the area highlighted in the sample above) looks like the link in the initial emai. It includes the sending company’s name, but this time it’s destination is not so safe.
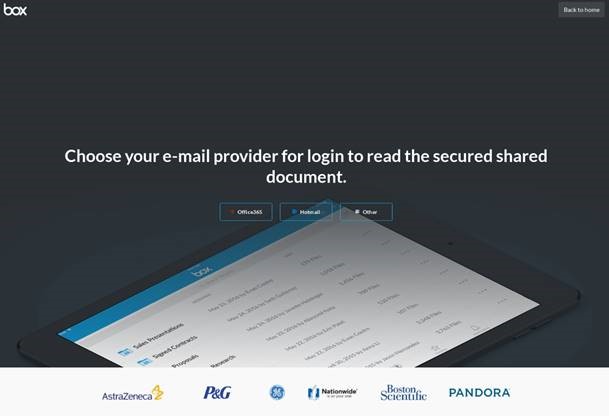
- The link will redirect you to a legitimate-looking Box.com login page, but it is a fake!
- This page prompts you to log in using email provider credentials. This is where your credentials get stolen. They now have access to your email, to credentials you may have reused on other sites, and and email address where you likely have password resets being sent.
__________
CORONAVIRUS IS OPPORTUNISTIC, AND SO ARE CYBER ATTACKERS
Cyber Attackers are heartless crooks attempting to exploit the Coronavirus situation to their benefit. They use the hype and anxiety about Coronavirus to improve the chances you will fall for a scam, click on a link, or download an app.
One tactic involves WhatsApp messaging app. Hackers lure users to click on links in WhatsApp messages containing malware. Once clicked, the malware infiltrates computers to steal passwords, financial info, and potentially spy on other activities useful to the threat actors’ future endeavors.
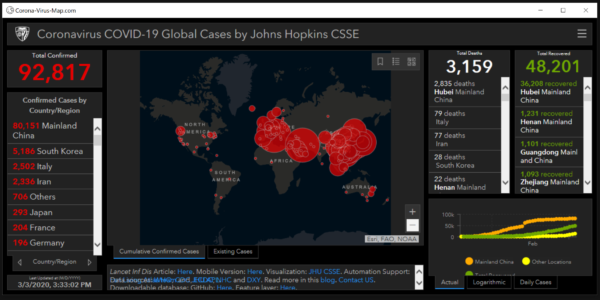
Via another method, criminals are taking advantage of the fixation on Coronavirus maps. They created infectious and official looking Coronavirus map websites. One such site contained malware called “AZORult” and was directly disseminating it to website visitors. AZORult sniffs out useful information and then drops other malware on the computers for future exploits. These attckers take advantage of you now and leave behind a method to do so in the future.
Smartphones are not safe from Coronavirus based attacks either. One threat group that took over a legitimate Coronavirus website and advertised a map app download with malicious contents.
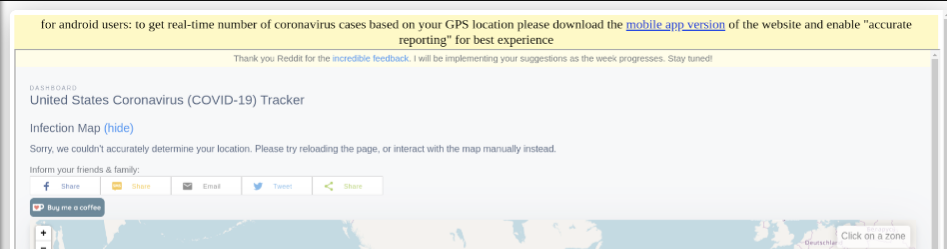
When clicking the link, it drops “COVIDLOCK” ransomware on the phone. COVIDLOCK tricks the user into changing their password and then locks the device. The ransomware demand follows quickly with a 48-hour window to pay .
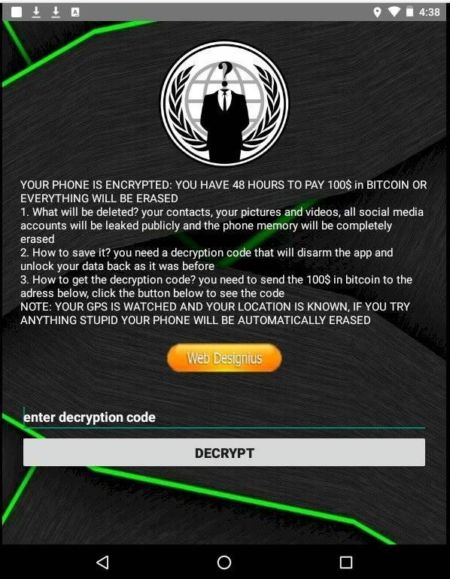
Avoid being duped by the Coronavirus hype cycle. Don’t let your curiosity about Coronavirus make things more complicated than they already are. Stick to well-known and reputable news sources for updated information.
If you run into trouble, Contact Runwell Solutions today at 610-376-7773 to get the computer help you need and protection you must have.



